This section provides orientation on managing integration tasks, available through the Administration module.
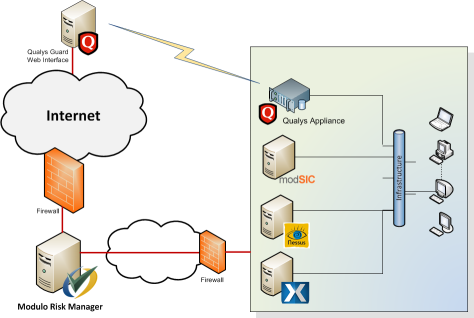
A number of external services can be integrated and synchronized with the system, extending the application’s functionalities by obtaining information outside of the system and executing requests. You can, for example, import the results of a vulnerability scan from an external service or update the user database from a certain domain, among others. The figure below illustrates how the integrations with external scanners and modSIC, Modulo's collector service, are structured.

Listed below are the types of integration tasks currently available in the system:
•Import Objects from Directory (LDAP): Creates a routine for importing users, groups, and technology assets from a certain domain.
•Import Assets from XML File: Creates a routine to import assets from files in XML format. When the task is configured, mappings must be provided to determine which fields from the XML file will be used to complete which asset properties and attributes.
•Dashboard Integration Service: Creates a routine for exporting system data to the Dashboard module, which uses a separate database to store the information displayed in charts. This allows the latest information to be displayed in the system.
•Import Events from XML File: Creates a routine to import events from XML files, allowing events listed in these files to be automatically registered in the Workflow module. When configuring the task, mappings must be provided for the system to correctly interpret the report and import the data.
•Live Update Service: Creates a routine for automatically checking if there is new content to be imported or updated. This content is generally provided with the system installation, but may also be imported and updated using this service. It includes authoritative documents, knowledge bases, and threats, among others.
•Import Assets from NeXpose Scanner: Creates a routine for importing and updating technology assets from a NeXpose inventory.
•Import Vulnerabilities from NeXpose Scanner: Creates a routine for importing vulnerabilities detected by a NeXpose scanner.
•Import Assets from Qualys Scanner: Creates a routine for importing and updating technology assets from a Qualys inventory.
•Import Vulnerabilities from Qualys Scanner: Creates a routine for importing vulnerabilities detected by a Qualys scanner.
•Synchronize Qualys Scanner Remediation: Creates a routine for updating or closing events in the Workflow module created to treat vulnerabilities. These events are closed if the corresponding ticket for the vulnerability in Qualys is resolved. In the case of consolidated events treating multiple vulnerabilities, the progress of the event is updated to indicate that a certain vulnerability was resolved.
•Export Queries to SQL Tables: Creates a routine to export the results of queries from the ERM solution and the Organization, Risk, Compliance, Workflow and Administration modules to SQL tables, which can later be used in custom charts for dashboards, for example.
•Import Vulnerabilities from XML File: Creates a routine to import occurrences of vulnerabilities from XML reports generated by scanners. When configuring the task, mappings must be provided for the system to correctly interpret the report and import the data to the catalog of vulnerabilities.
•Execute HTTP Call: Establishes a connection with an HTTP server and creates a routine to request or send data to a specific resource through the GET and POST request methods.
•Run SQL Script: Create a routine to extract data from the Modulo Risk Manager databases through a SQL script. The data will be processed and stored in an external database that can be accessed for creating custom reports and charts, for example.
Note: To streamline task execution and prevent errors, integration tasks of the same type must be executed at different times. It is recommended that the execution time of each task be considered when scheduling them. To do this, you can execute a task separately, record its execution time, and schedule it with enough time so that its execution is completed before the next task execution begins. This should also be taken into account in tasks scheduled to be executed frequently (every minute, for example), as it is important to ensure that the time interval between the schedules of the same task is longer than its execution time. Tasks of different types scheduled for the same time are executed simultaneously.