This topic explains how to create an integration task with QualysGuard scanners, which creates a routine for importing vulnerabilities detected by a certain vulnerability analysis performed with QualysGuard.
QualysGuard is a software program used to help automate the vulnerability management lifecycle for technology assets. It includes features to:
•Map networks, identifying the organization’s technology assets.
•Scan vulnerabilities in machines on the network, prioritizing the most relevant assets.
•Store the results of the scans in the QualysGuard environment.
Modulo Risk Manager provides a way to manage vulnerabilities in the organization by allowing vulnerabilities discovered by QualysGuard to be checked by means of graphs and reports provided for technology assets. These are shown under the Vulnerabilities tab through graphs for individual assets or consolidated by perimeter. Vulnerability data is displayed on the same graph even if more than one vulnerability scanner was integrated with the system (for example, Qualys, NeXpose, etc.). The list of vulnerabilities will identify which vulnerability was identified by which service. Note that if two or more vulnerability scanners scan the same objects, the information will not be consolidated and there will likely be duplicate vulnerabilities reports for the scanned objects.
In addition to displaying these vulnerabilities in the Organization module, technology assets can be included in the scope of vulnerabilities of risk project. Any vulnerabilities associated with these assets can then be evaluated so that analysts can decide whether they will be accepted or sent to treatment.
Any vulnerabilities identified for assets are also automatically included in the catalogue of vulnerabilities in the Risk Knowledge section of the Knowledge module. Vulnerabilities from scanners not supported by the system can also be manually imported to the catalogue and mapped to assets through spreadsheets. For details on manually including vulnerabilities to the catalogue, see Chapter 8: Knowledge -> Risk Knowledge -> Catalogue of Vulnerabilities. For details on manually mapping vulnerabilities from the catalogue to assets, see Chapter 5: Risk -> Vulnerability Occurrences.
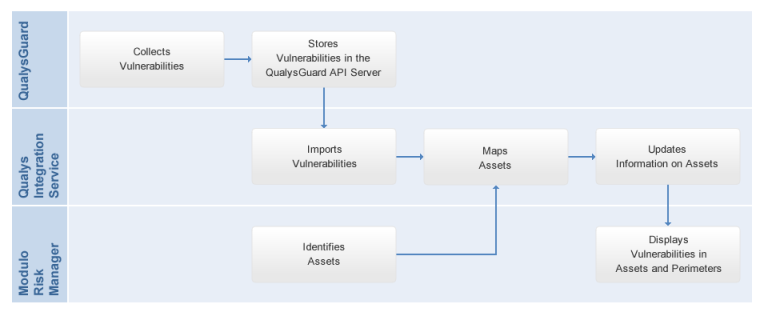
The vulnerabilities collected by QualysGuard can be recovered and stored by the system (see figure below). Note that the time it takes to scan the inventory selected and generate a report in Qualys must be less than the interval set for the integration task.

The integration service for QualysGuard queries information on this solution’s database using the QualysGuard API. Requests through this API are performed through HTTP, which in turn transports the content in XML. Keep in mind that, for the information to be imported successfully, users registered in the Qualys website must first enable the API checkbox in the User Role option when editing users. Further details can be viewed on the Qualys website.
The match between the equipment scanned by a Qualys scanner and the corresponding technology asset in Modulo Risk Manager is according to the asset mapping criteria specified in the Properties tab for each perimeter or for each asset individually. If there is no match between a vulnerability identified for a certain machine and an asset in the system, the integration task history will show the number of assets that were not associated with vulnerabilities due to this problem of identification.
When creating an integration task of this type, you can select an option that allows notifications to be generated in the system when inconsistencies occur regarding the existence of vulnerabilities imported through the task and later sent to treatment. For instance, if a vulnerability is identified through a scan, imported and mapped to an asset through this integration task, and then sent to treatment through a risk project, the system will display notifications if the vulnerability is not found in subsequent executions of that same scan. These notifications will appear in the risk project through which the vulnerability was sent to treatment, in the Home module for the user that was assigned as project leader, and in the Progress and Associations tabs of the event created to treat the vulnerability.
These notifications will also be generated when an asset in the scope of the risk project is removed from the scope of a scan. This occurs because the vulnerabilities identified for that asset are no longer found, not necessarily because they do not exist but because the asset is no longer being analyzed by the scanner in that particular report. If the assets were purposely removed, the scan report should be renamed so as to prevent notifications from being generated erroneously. In addition, if different credentials or a different policy is used to access and scan the assets, this could prevent certain vulnerabilities from being again identified and generate erroneous notifications.