This section provides orientation on managing asset risks, available through the Risk module.
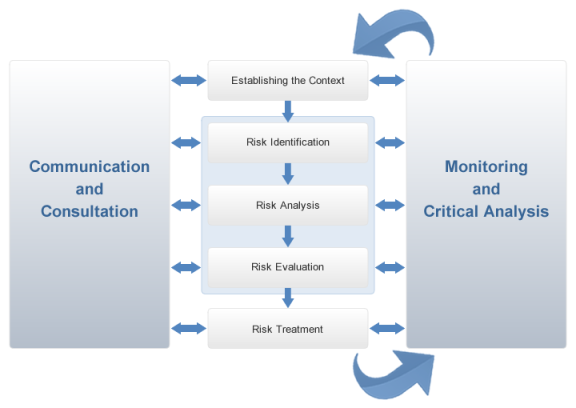
ISO 31000 – Risk Management – Principles and Guidelines defines risk as the effect of uncertainty on the objectives, where the effect is a deviation in relation to what is expected, be it positive or negative. According to this standard, the objectives may have different aspects (such as financial, health, safety, and environmental goals) and may apply to different levels (such as strategic levels, the entire organization, projects, products, or processes) (see figure below).

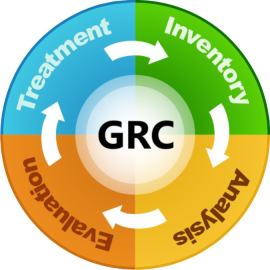
Modulo Risk Manager, in accordance with the guidelines provided by the ISO 31000 and ISO Guide 73 – Risk Management – Vocabulary, adopts a risk management cycle based on the following phases:
•Inventory: set of actions required to establish the properties and scope of each risk management project, including the assets and asset components that will be analyzed and by whom.
•Analysis: set of actions required for collecting data to identify risks in the assets selected for the scope of the project.
•Evaluation: the decision process to accept risks or send risks considered unacceptable to treatment.
•Treatment: the process of monitoring the risk treatment events generated during the evaluation phase.
Risk management projects are created to determine the level of exposure of the organization's assets to existing threats and quantify the impact the organization is subject to if the vulnerabilities of assets are exploited by harmful agents. Projects can be viewed, created, edited, closed, cancelled, deleted, and reopened through the Risk module.
Each of the risk management phases may be monitored, since the system includes the functions required to integrate the phases into a single project: inventory, analysis, evaluation, and treatment.
Through reports, dashboards, and queries, detailed information on the results of analyses can be viewed. Use of these tools allows for increased productivity, control, and standardization of activities, and assists organizations in achieving the desired results.
Risk projects can be control-based, vulnerability-based, or both. In the first, asset components previously associated with knowledge bases are included in the scope of the project so that analysts can verify whether the controls (good practices) from the questionnaire related to that asset component are implemented. If they are not implemented, risks could be exploited by the threats related to them.
In the case of a vulnerability-based project, the scope is created by selecting technology assets to which vulnerabilities were previously mapped. These vulnerabilities are identified by external scanners and can be automatically or manually mapped to their corresponding assets in the organizational structure. These assets can then be included in the scope of vulnerabilities for the project so that analysts can decide whether to accept or treat their associated vulnerabilities – from which point the normal risk management cycle continues. For details on integration tasks to automatically import and map vulnerabilities detected by scanners to assets, see Chapter 17: Administration -> Integrations -> Integration Tasks. For details on importing vulnerabilities to the catalogue, see Chapter 8: Knowledge -> Risk Knowledge -> Catalogue of Vulnerabilities. Lastly, for details on manually mapping vulnerabilities identified by scanners not supported by the system to assets, see Chapter 5: Risk -> Vulnerability Occurrences.