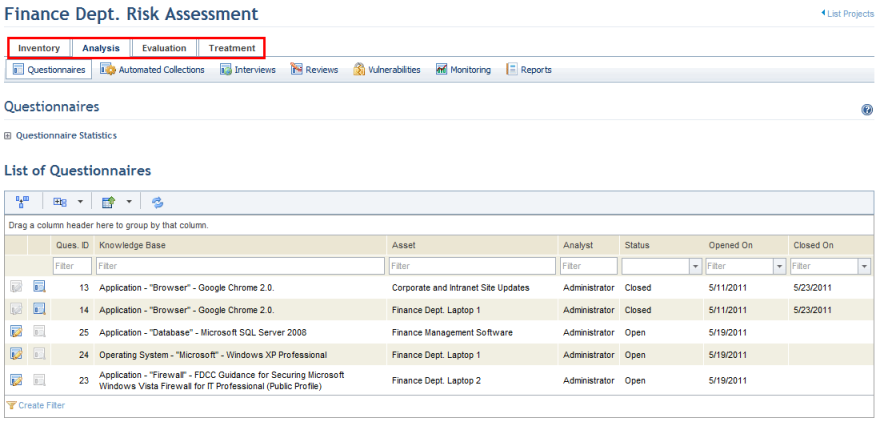
•GRC Metaframework Cycle for Projects: Risk and compliance projects can be created from scratch or from copies of existing projects to analyze any type of organizational object in an interface that is fully compatible with the GRC Metaframework methodology, which includes the inventory -> analysis -> evaluation -> treatment cycle.
The product supports questionnaire- and vulnerability-based risk assessments for different types of assets and uses different metrics according to the type of information to be analyzed. These metrics support the decision-making process on which risks are at an acceptable level and which should be treated. The scope of risk assessments can be freely configured and include components of all types of assets.
Compliance assessments are survey-based and offer support for implementing certification requirements for SOX, PCI-DSS, ISO 27002, ISO 27001, BS 25999, COBIT, Basel II, HIPAA, OCC, SEC, NERC, and FISAP while significantly reducing the cost and time of adjustment to good compliance practices, reducing costs of multiple audits, and eliminating redundant controls. The scope of assessments can include people, business components, and assets, and the metrics generated support prioritization of which requirements should be implemented.

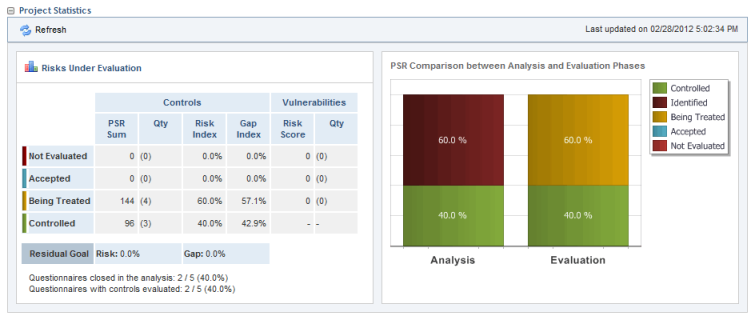
•Project Statistics: Graphs show statistics on projects and on each of their phases.
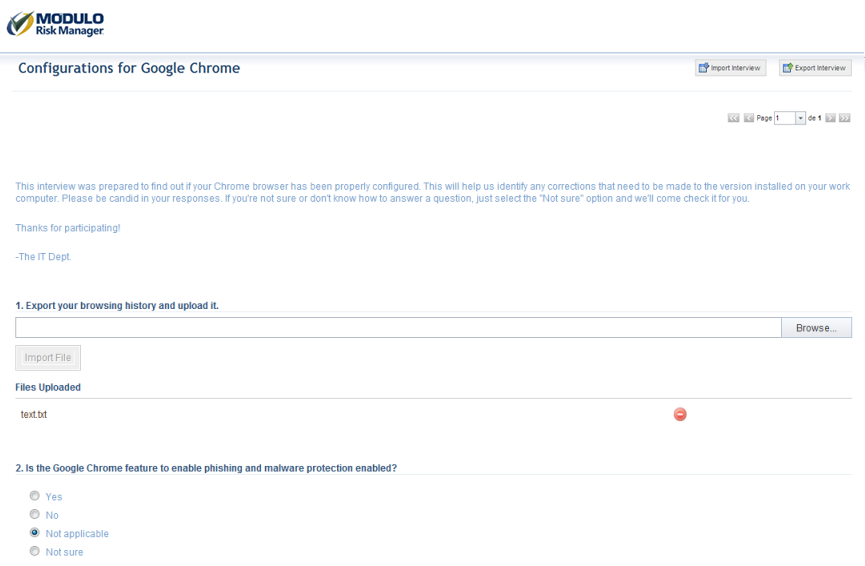
•Answer Risk Questionnaires Online or Off: A user-friendly interface is available for answering questionnaires online. These questionnaires can also be answered offline through a spreadsheet or through a mobile device.
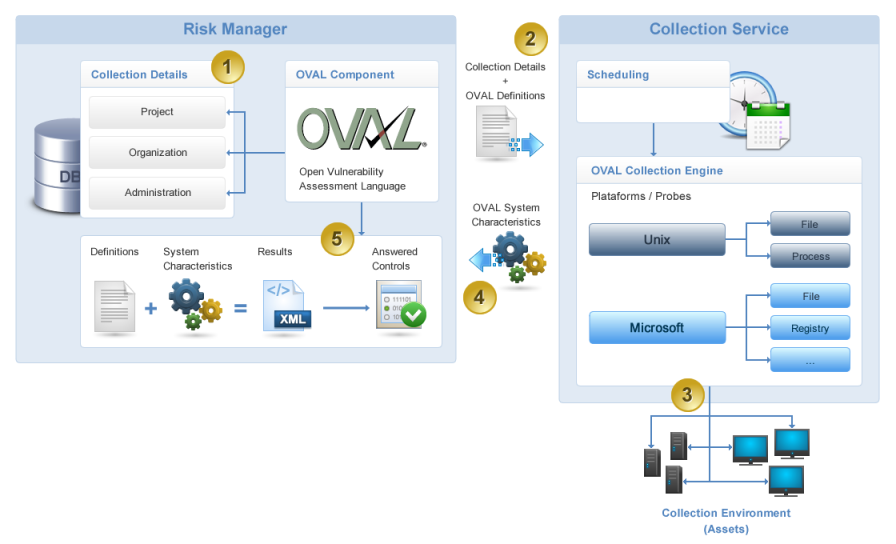
•Automated Collections in IT Assets via OVAL: Evidence of flaws in security configurations in technology assets can be collected and stored automatically, and this information is then used to automatically answer certain controls in risk questionnaires. Modulo’s collector service, modSIC, must be installed on a server to run and manage collections. Once collector servers and access credentials for the target machines are registered in the Administration module, you can request a collection. The system provides OVAL-based automated collectors for a number of technologies, such as MS Internet Explorer 11, MS Office 2016, MS SQL Server 2016, MS Windows 8.1, MS Windows 10, MS Windows Server 2016, Oracle Database 12c, Red Hat Enterprise Linux 7, Ubuntu Linux 16, CentOS Linux 7, Oracle Linux 7, Debian Linux 8, Apache Web Server 2.4, and others.
The request for a collection can be scheduled to run during off-hours, when target machines are not being heavily used. The collector server receives these requests, organizes the collections for each project, runs the collections, and, when the collections are finished, sends the results back to the system. Communication between the system and the collector server involves the exchange of files that use the OVAL (Open Vulnerability and Assessment Language) standard, developed by MITRE (https://oval.mitre.org/).
No installations of agents or components in the network’s assets are needed, and these collections are passive such that no information is modified in the target machines. The process takes place transparently and automatically as long as the credentials provided are valid and the collector server is able to connect to the target machine.
•Analyze Vulnerabilities in Risk Projects: Vulnerabilities identified by external scanners or imported manually can be mapped to assets, and these assets can be included in risk projects. The vulnerabilities identified for each can then enter the risk management cycle, where you can decide to accept them or manage their remediation through treatment events in the Workflow module.
•Answer and Review Interviews: Interviewees and reviewers are assigned in risk and compliance projects to answer interviews on specific objects that have been added to the scope of the project. The workflows for sending interviews are fully manageable from projects themselves and the system offers a number of notifications to ensure an efficient process. Each interview can be sent immediately or scheduled to be sent at a certain date and time. Responses are processed automatically by the system and can be queried in detail. Comments or attachments provided as evidence in interviews can be automatically attached to questionnaire controls and viewed by analysts. These interviews and reviews can be re-sent to interviewees and reviewers once finalized, if necessary. Each interview can be exported to a spreadsheet, answered offline, and imported back to the system. In addition, interviewees and reviewers can choose to download or receive by e-mail documents with proof of interview completion and the list of responses provided after answering or reviewing interviews assigned to them.
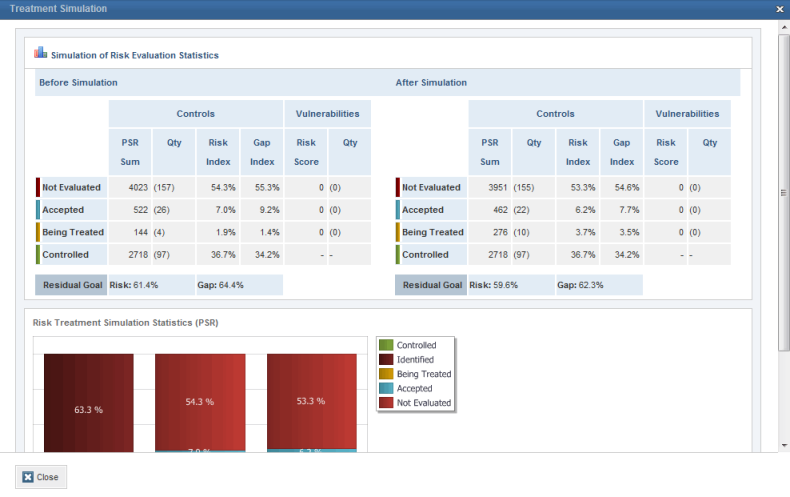
•What-If Simulator: A What-if simulator can be used to assist in decisions to treat or accept risks. The simulation shows the risk indices that would be true if the non-implemented controls selected were treated.
•Evaluate Risks and Non-Compliances: The product offers the adequate means to evaluate risks and non-compliances through a process that considers the consolidated results of assessments and the indicators obtained. For each risk or non-compliance, managers can determine whether they should be accepted or treated, and justification must be provided before they can be accepted.
•Treat Risks and Non-Compliances: Events in the Workflow module can be created individually or collectively to manage remediation of non-compliances and risks identified in the projects. A number of customizable notifications are provided to ensure a streamlined process.
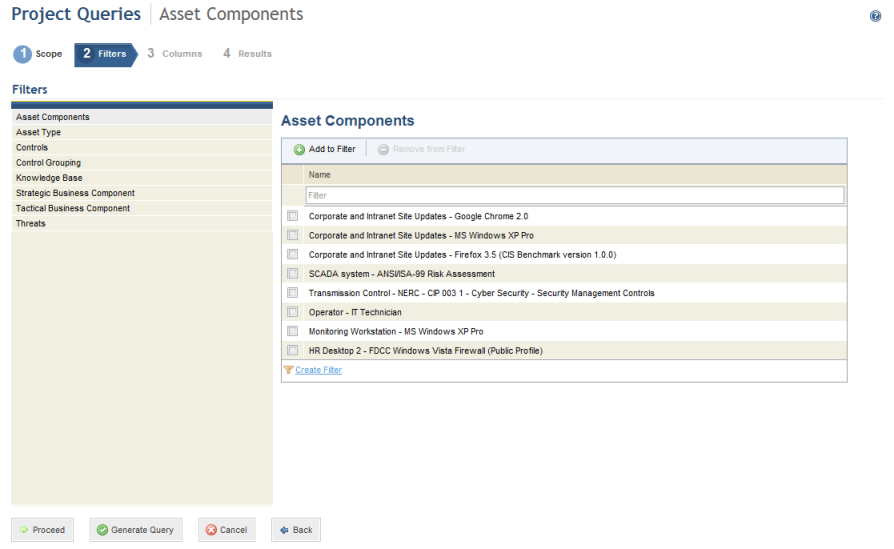
•Query Analysis Results: The results of risk and compliance projects can be queried in detail. The system provides a wizard to help create these queries, the results of which can be viewed through tables, maps, or through the integrated overview, for queries consolidated by asset. Each query can also be copied so that its configurations can be reused in new queries. In addition, people and groups of people can be assigned as audience members or editors of each query so that they can view or edit it.
•Customized Reports: The system allows reports to be created, customized, and generated for different audiences. These show the latest results of the analyses from one or more projects. Reports can be filtered and, once generated, can be exported to various formats or sent via e-mail. Schedules can also be created for them so that they are generated and sent at a certain frequency to certain recipients. In addition, SQL queries to the system database and to external databases can be written and inserted in these reports so that new tables and charts can be included in each.
