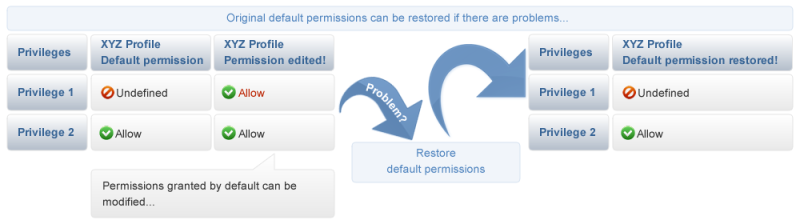
Although the permissions granted by default are designed to meet the needs of most use cases, the system allows these permissions to be edited. However, modifying these default permissions should be done with caution. Inappropriate modifications may compromise security (inappropriately allowing access) and may also result in blocked access for users who should be authorized to perform certain operations. In the event that changes made to permissions produce undesirable results, the default permissions can be restored (see figure below).
