As in the case of inclusion in profiles, people or groups of people assigned to a role inherit the permissions granted to the privileges associated with the role. However, in this case there will always be a condition or context to be verified before the permission is granted, as mentioned previously: Allow {Privilege} if {condition for granting privilege}.
In the example below, Knowledge Managers is a profile, which has explicit permission ("allowed") to the Edit Knowledge Bases privilege. Accordingly, all people and groups of people included in this profile automatically inherit this permission, and may manage (view, register, edit, and delete) any knowledge base.
|
Permissions to Privileges for Profiles and Roles | |
|
Profile - Knowledge Managers
|
Role - Responsible for Knowledge Base
|
|
Allowed |
Allowed…but only knowledge bases for which the person is responsible. |
On the other hand, Responsible for Knowledge Base is a role to which people or groups may be assigned. In this case, even though permission is being explicitly granted to this role in the same privilege (Edit Knowledge Bases), there is an additional condition that must be verified by the system before permission is granted: the person or group who exercises this role will only be edit knowledge bases to which they were assigned as responsible, and not any knowledge base in the system.
In other words, while exercising the role of responsible for XYZ knowledge base, a user – for example, John Smith – will automatically receive permission to the Edit Knowledge Bases privilege, valid only for the XYZ knowledge base. Once John Smith stops exercising this role (for example, someone else is assigned as responsible for the knowledge base), he will lose the privilege.
As in the case of profiles, a person or group of people may simultaneously exercise various roles in the system. In this case, the person or group will cumulatively inherit permissions granted to the roles to which they were assigned (see figure below).
The system administrator does not need to worry about the technical details of granting conditional permissions to roles, since this is handled automatically and transparently by the system.

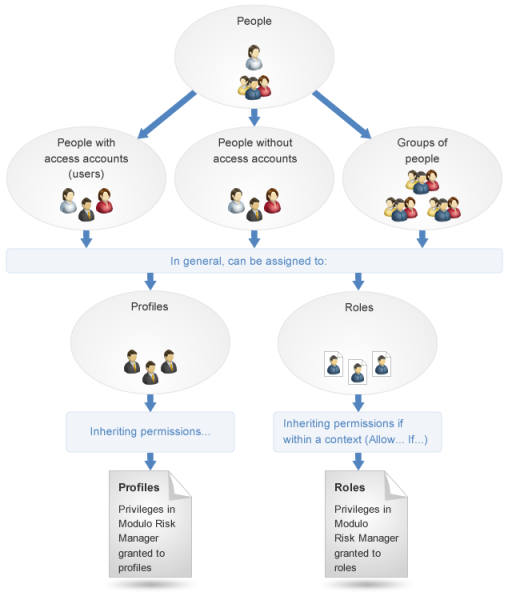
The system does not allow permissions to privileges to be directly granted to any one person or group of people. The only way to obtain permissions is through inheritance, by being included in a profile or being assigned to a role.
Also note that because profiles have an administrative or managerial functions (managing and configuring the various system modules and solutions), it is recommended that they include only users (people with system accounts). For most roles, an account is also recommended for methodological reasons (for example, it is expected that users assigned as Leader of a Risk Management Project be able to access the system in order to lead the project). However, the system allows people without system accounts to be included in profiles and to be assigned to roles, and groups of people who include people without system accounts can also be included in profiles and assigned to roles.