This topic explains how to view the catalogue of vulnerabilities, which includes vulnerabilities identified in technology assets by external scanners integrated with the system as well as any that were manually imported.
1. Access the Knowledge module.
2. Select Catalogue of Vulnerabilities from the Risk Knowledge option on the menu.
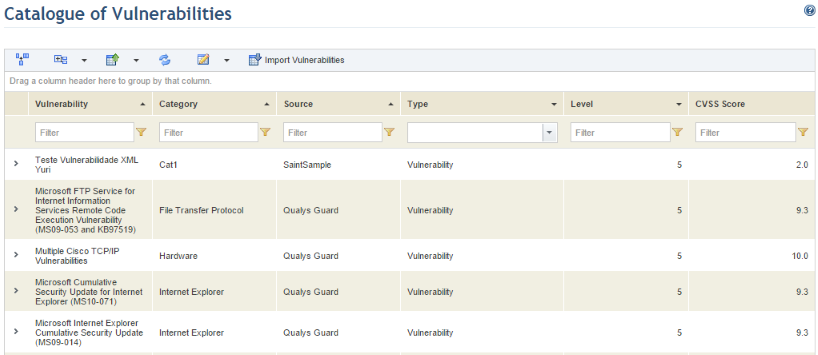
The system displays the list of vulnerabilities (see figure below).

Note: The information displayed in each of the columns included in this section is detailed below:
•Vulnerability: lists the name of the vulnerability as registered in the scanners or as specified when the vulnerability was imported to the system.
•Category: indicates the group of vulnerabilities to which the vulnerability in question belongs. Note that the NeXpose scanner does not use categories, thus in this case only the scanner name will appear in this column.
•Source: indicates the scanner used to perform the vulnerability analysis or the source listed on the spreadsheet when the vulnerabilities were imported.
•Type: indicates the type of vulnerability, either Information Gathered (additional information collected on the technology asset), Potential Vulnerability (possible, unconfirmed vulnerabilities), and Vulnerability (confirmed vulnerabilities).
•Level: indicates the vulnerability’s severity level on a scale of 1 (Very Low) to 5 (Very High). The three different metrics used by the scanners that were integrated with the system are normalized to the internal scale as follows:
|
QualysGuard Level: |
NeXpose Level: |
Modulo Risk Manager Level: |
|
1 |
1 – 2 |
1 |
|
2 |
3 – 4 |
2 |
|
3 |
5 – 6 |
3 |
|
4 |
7 – 8 |
4 |
|
5 |
9 - 10 |
5 |
•CVSS Score: indicates the Common Vulnerability Scoring System, created by the National Infrastructure Advisory Council (NIAC). This is an index from 0 to 10 that determines the urgency, priority, and severity of the vulnerabilities encountered. The CVSS score can be one of three types (base, temporal, or environmental). The type used by the system is CVSS base metrics.
•Last Updated: indicates the date on which information on the vulnerability was last updated.
•Vulnerability ID: provides the vulnerability’s ID according to its source.
3.
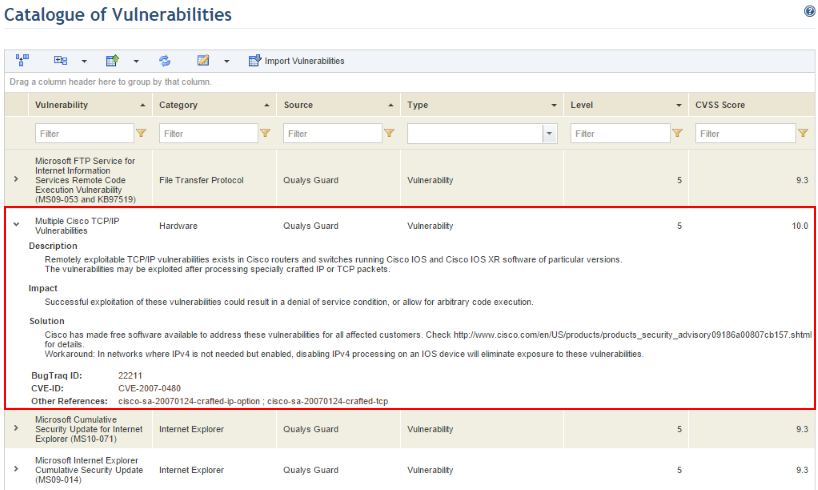
To view details on a vulnerability, click Expand ( ) next to it.
) next to it.
The system displays details on the vulnerability, including its description, impact, solution, Bugtraq ID, CVE ID, and other references (see figure below).