1. Access the Risk module.
2. In the Risk Management Projects section, click the List Projects option.
3. In the Risk Management Projects section, click Edit next to the risk management project containing the vulnerabilities you want to treat.
4. Click the Evaluation tab.
5. Click the List of Vulnerabilities tab.
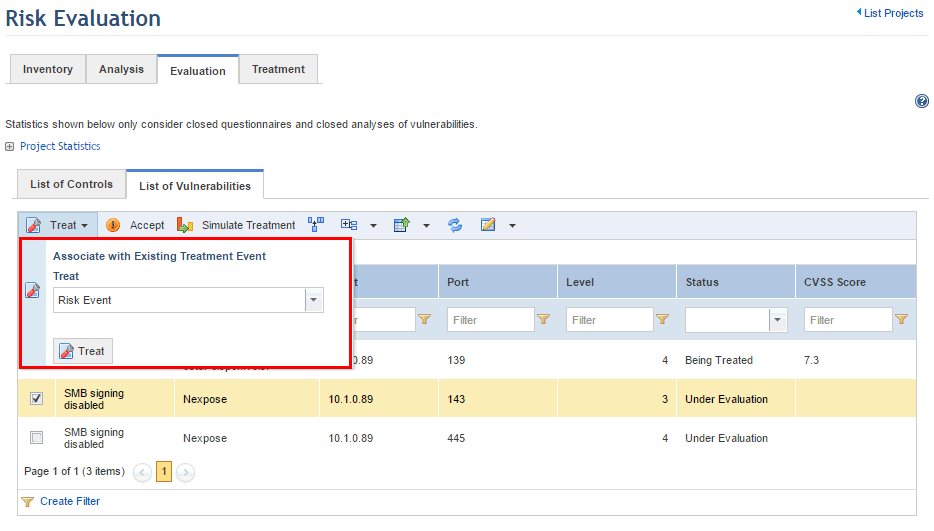
6. Mark the checkboxes next to the vulnerabilities you want to send to treatment, click Treat, and select the Associate with Existing Treatment Event option to use an existing treatment event, or select an event type from the drop-down menu and then click Treat to create a new event . Note that you will only be able to view event types for which the association with controls and vulnerabilities was previously enabled in the Object Types section of the Administration module.

Note: The Status in Previous Project column allows you to check whether the vulnerability you want to treat is included in another project. This column option displays the most recent information for the vulnerability in another project, including its status and the project code. If a treatment event was created for it, the event code will also be displayed, which can help you decide whether a new event should be created or if the risk should be associated with the existing event.
If you opted for using an existing event, the system will display a success message indicating that the vulnerabilities selected were associated. Note that the vulnerabilities will not be associated if an open treatment event is not found, in which case you will need to accept the vulnerability or create a new treatment event.
When the Treat option is selected, the system displays the form used to create events (see figure below).
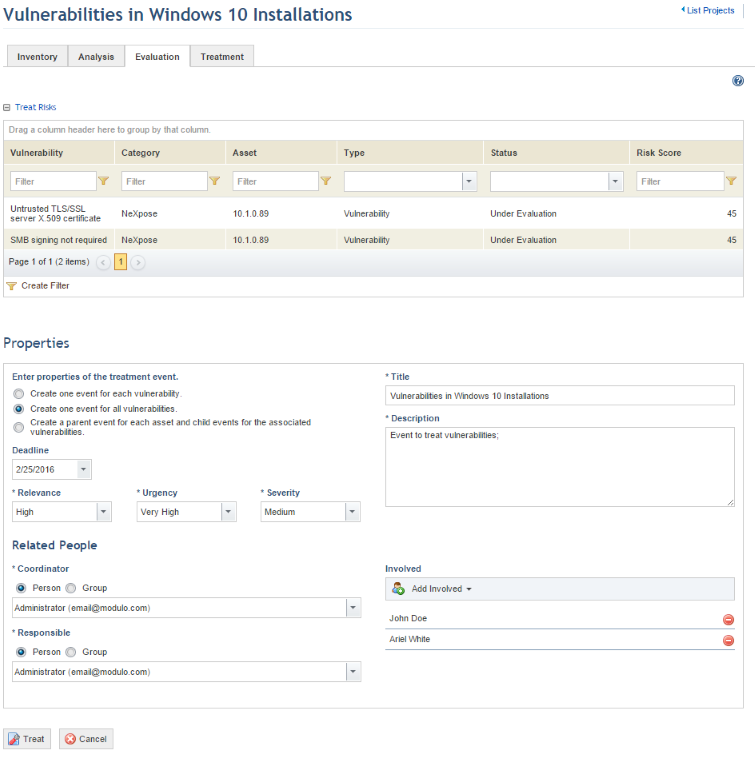
7. Select Create one event for each vulnerability if you want to create a treatment event for each vulnerability selected. This option will only be enabled if more than one vulnerability is selected.
8. Select Create one event for all vulnerabilities if you want to consolidate treatment of multiple vulnerabilities. This option will only be enabled if more than one vulnerability is selected.
9. Select Create a parent event for each asset and child events for the associated vulnerabilities to create a parent event for each asset and child events for each of the vulnerabilities related to the asset. This option will only be enabled if more than one vulnerability is selected.
10. In the Deadline field, select the deadline for the event. This field is optional and can be edited later, if necessary. This deadline will be applied to all events being created.
11. In the Relevance field, specify the relevance for the event, which will be used to calculate the USR.
12. In the Urgency field, specify the urgency for the event, which will be used to calculate the USR.
13. In the Severity field, specify the severity for the event, which will be used to calculate the USR.
14. In the Title field, enter a name for the event using up to 2,500 characters to help easily identify it in the list of events in the Workflow module.
•If only one vulnerability was selected, the default title will be the name of the vulnerability. Note that this field can be edited afterwards.
•If more than one vulnerability was selected but individual events are being created for each, this field will be disabled and the title of each event will be the name of each respective vulnerability.
•If more than one vulnerability was selected and a consolidated event is being created for them, this field will need to be completed.
•If a parent event is being created for each asset and child events for the vulnerabilities, this field will be disabled. The name of the parent event will be the project code together with the name of the asset, while the name of each child event will be the name of each respective vulnerability.
15. In the Description field, enter information describing the event using up to 5,500 characters.
•If only one vulnerability was selected, the description of the event will be the same as that of the vulnerability, by default. Note that this field can be edited afterwards.
•If more than one vulnerability was selected but individual events are being created for each, this field will be disabled and the description of each event will be the description of each respective vulnerability.
•If more than one vulnerability was selected and a consolidated event is being created for them, this field will need to be completed.
•If a parent event is being created for each asset and child events for the vulnerabilities, this field will be disabled. The description of the parent event will be the project code together with the name of the asset, along with the number of child events created. The description of the child events will be the description of each of the respective vulnerabilities.
16. In the Coordinator field, select the person or group of people who will be assigned to carry out the event and update its progress. By default, if the same person was assigned as responsible for all assets related to the vulnerabilities being treated, this person will also be assigned coordinator of the treatment events. On the other hand, if different people were assigned as responsible for each asset, the person who sends the vulnerabilities to treatment will be assigned as coordinator of all treatment events being created.
17. In the Responsible field, select the person or group of people assigned to perform activities and update information on the event’s progress. By default, if the same person was assigned as responsible for all assets related to the vulnerabilities being treated, this person will also be assigned as responsible for the treatment events. On the other hand, if different people were assigned as responsible for each asset, the person who sends the vulnerabilities to treatment will be assigned as responsible for all treatment events being created.
18. In the Involved field, select the person or group of people who will be formally involved with the event while it takes place. Keep in mind that the people or groups selected here will be involved in all events being created.
Note: Event Coordinator, Event Author, Responsible for Event, and Involved in Event are access control roles. Those assigned to these roles will automatically inherit permissions in their respective events. Keep in mind that you can restrict list of members who can be included in these roles through the Roles Restrictions section of the Administration module. If role assignment is restricted for the event type selected, only the people or groups included in the list of members can be assigned to these roles. For details, see Chapter 17: Administration -> Access Control -> Access Control Concepts and Chapter 17: Administration -> Access Control -> Role Restrictions.
19. When finished, click Treat to send the vulnerabilities to treatment. If you want to quit the operation, click Cancel.
The system displays a success message and returns to the list of vulnerabilities. The event author will receive a notification in the Home module indicating that events were successfully created in the Workflow module. At this point, the codes of these events will be listed in the Treatment tab. Note that although the status and progress of each event can be monitored through the Treatment tab, these events can only be managed in the Workflow module.
Note 1: When vulnerabilities are sent to treatment, the assets related to them are associated with the events and can be viewed through the Associations tab of each. Any business components that were associated with these assets will also be associated with the events.
Note 2: There is an important correlation between the status of a treatment event and the status of the associated risk, indicated in the table below:
|
Treatment Event Status |
Effect on Associated Risk |
|
Closed |
The risk that was before considered Being Treated in the Evaluation and Treatment tabs is then considered Treated. |
|
Cancelled |
The risk that was before considered Being Treated in the Evaluation and Treatment tabs is then considered Not Evaluated in both tabs. Note that cancelled events cannot be reopened, while closed events can. |
|
Reopened |
If a treatment event is reopened, the risk that was before considered Treated in the Evaluation and Treatment tabs returns to Being Treated. |