This topic explains how to register the Workflow app as an authorized application so it can access system features through the API. Once the application has been registered in the system, it can be used in an Android device to list and manage events.
1. Access the Administration module.
2. Select Authorized Applications from the Integrations section on the menu.
3. In the Manage Authorized Applications section, click Add Application.
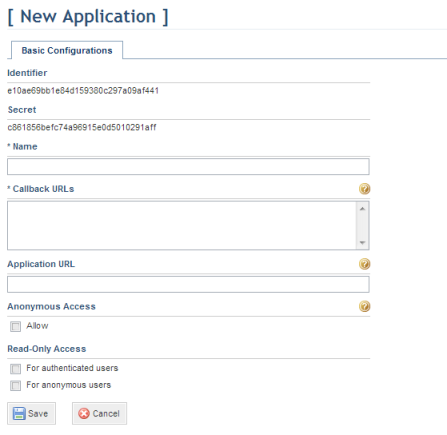
The system displays the Basic Configurations tab, where information on the application to be registered should be entered (see figure below).

4. In the Name field, enter the name to be used to identify the Workflow app using up to 100 characters. This field is required.
5. In the Callback URLs field, enter "workflow://auth", which will be the address where the app will receive callback data from the system.
6. Leave the Application URL field blank.
7. Leave the Allow checkbox from the Anonymous Access section blank, since all application users will need to provide their system access credentials.
8. In the Read-Only Access section, mark the For authenticated users checkbox if you want to only allow read-only access to the events. In this case they will not be able to update or create new events.
9. Before saving, write down the identifier and secret key generated for the application, as this information will be used later on.
10. When finished, click Save. If you want to quit the operation, click Cancel.
The system enables the Available Features, Advanced Configurations, and Active Tokens tabs.
11. Click the Available Features tab to select the features which the app will be allowed to access.
12. Mark the checkbox next to List events from the Workflow module. This will allow the app to access the events in this module.
13. Mark the checkbox next to Manage events from the Workflow module. This will allow events to be created and updated through the app (see figure below).
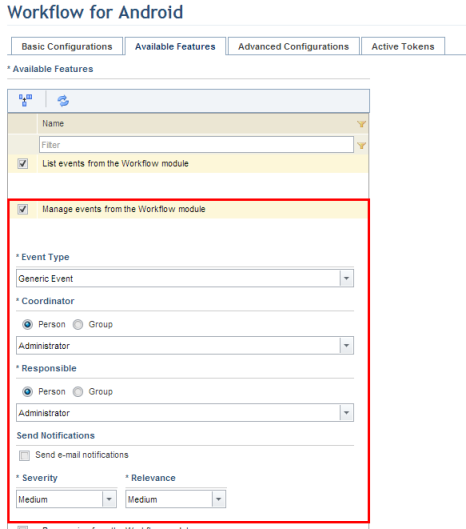
14. In the Type of Event field, specify the type of event to be applied to all events originating from this app. This field is required.
15. In the Coordinator field, select the person or group to be assigned as coordinator for all events originating from the authorized application. This field is required.
16. In the Responsible field, select the person or group to be responsible for all events originating from the authorized application. This field is required.
17. If you want to allow notifications to be sent regarding these events, mark the Send e-mail notifications checkbox. In order for notifications to be sent via e-mail, the message service must be configured in the Message Service section of the Administration module; message templates regarding events must be enabled in the Message Templates section of the Administration module; and a valid e-mail address must have been provided for people in the Manage People section of the Organization module. Notification messages regarding events also appear in the Notifications section of the Home module.
18. In the Severity field, set the default severity (S) for all events originating from the authorized application, in other words, the impact that not treating the event will have on the organization. This is scored on a scale from 1 to 5, with: 1 - Very Low, 2 - Low, 3 - Medium, 4 - High, and 5 - Very High. Note that the severity score of an event can be updated while editing the event through the app.
19. In the Relevance field, set the default relevance (R) for all events originating from the authorized application. This is scored on a scale from 1 to 5, with: 1 - Very Low, 2 - Low, 3 - Medium, 4 - High, and 5 - Very High. Note that the relevance score of an event can be updated while editing the event through the app.
20. When finished, click Save. If you want to quit the operation, click Cancel.
The system displays a success message.
21. Click the Advanced Configurations tab to specify some additional features related to the authentication process (see figure below).
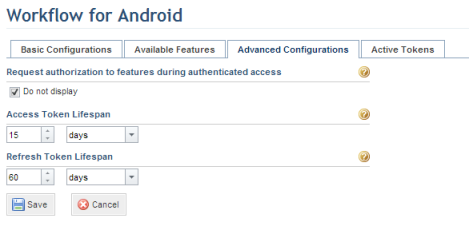
22. In the Request authorization to features during authenticated access section, mark the Do not display checkbox if you do not want the authorization screen requesting access to the features to be displayed. In this case, the system will trust the app and will grant access to the selected features.
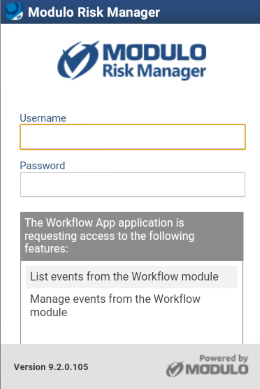
23. If you choose to show this authorization screen with the list of features, you can enter a customized message in the Customized message to request authorization during authenticated access field. This message will be displayed instead of the default list of features in the screen to authorize the application to access to the system (see figure below).
24. In the Access Token Lifespan section, specify the validity period for the access tokens issued by the system. An access token is used to grant authorized applications access to API features. For security reasons, the lifespan of the access token should be short, as it is sent in all calls to the API and can be used to access all the operations with the same username of the user who has access to these operations. Anonymous access tokens have the same lifespan, which, by default, is one day. In order to access the application, then, users will have to provide their usernames and passwords every day unless the token lifespan is extended.
25. In the Refresh Token Lifespan section, specify the validity period for the access token to be updated. Once the token has expired, users will have to provide their usernames and passwords to access the application. The lifespan for the refresh token must be higher than the lifespan for the access token.
26. When finished, click Save. If you want to quit the operation, click Cancel.
The system displays a success message.
27. Click the Active Tokens tab to view the list of users with active tokens, the number of access and refresh tokens associated with each, and the date on which the most recent one was issued. Note that a single user may have more than one access token associated with their account if they accessed the system through the API using, for example, two different devices.
28. To delete the tokens associated with a user, mark the checkbox next to the user and click Delete Tokens. Note that in this case the user will need to again enter credentials to gain access to the system features.
The system requests confirmation of the deletion of the tokens (see figure below).
29. Click Delete Tokens to confirm. If you want to quit the operation, click Cancel.
The system displays a success message.
30. Click the List Applications link in the upper right corner to return to the main list of authorized applications.