1. Access the Risk module.
2. In the Risk Management Projects section, click the List Projects option.
3. In the List of Projects section, click Edit next to the risk management project for which you want to process the list of assets.
4. Click the Analysis tab.
5. Click Vulnerabilities.
6. Mark the Include "Information Gathered" vulnerabilities in the processing checkbox. By default, only "Vulnerability" and "Potential Vulnerability" vulnerabilities will be processed.
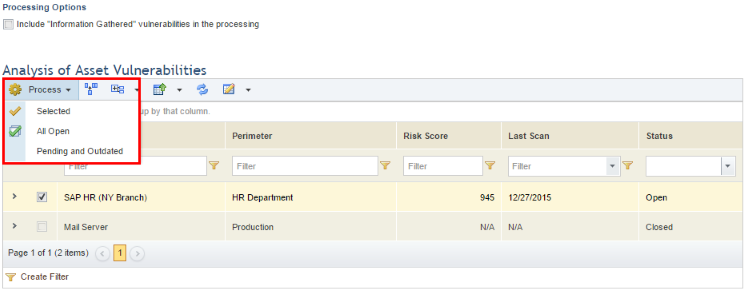
7. Click Process (see figure below).

Note 1: There are three options to process the list, which will update the vulnerabilities associated with the assets with information already imported to the system (from scanners or manually through spreadsheets), namely:
•Selected: Fetches the list of vulnerabilities for all the assets selected manually by marking the checkboxes next to each.
•All Open: Fetches the list of vulnerabilities for all assets with vulnerability analyses that are still open.
•Pending and Outdated: Fetches the list of vulnerabilities for all assets that have not yet been processed and any assets for which there is more recent information.
Note 2: If the relevance of an asset is changed in the Organization module, the Risk Score will only be recalculated when the asset is reprocessed.
If, for example, you choose to process the assets selected, the system requests confirmation (see figure below).
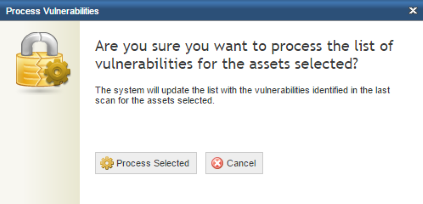
8. Click Process Selected to continue. If you want to quit the operation, click Cancel.
The system displays a success message and indicates the number of assets updated.
9.
To view the vulnerabilities associated with each asset, click Expand
( ) next to each.
) next to each.
The system displays the list of vulnerabilities identified for the asset grouped by the source of each (see figure below).
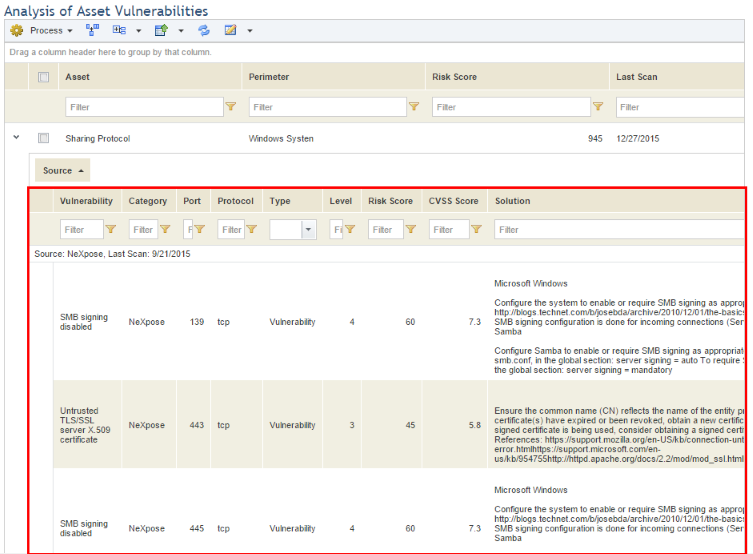
Note: The columns available on this page and their descriptions are listed below:
•Asset: Displays the name of a technology asset.
•Perimeter: Displays the name of the perimeter to which a technology asset belongs.
•Risk Score: Displays the Risk Score, which is calculated individually for each vulnerability and consolidated for the asset. For details on this metric and how to customize it, see Chapter 17: Administration -> Customizations -> Risk Score.
•Last Scan: Displays the date the asset was last analyzed by external scanners.
•Status: Displays the status of the analysis of vulnerabilities for an asset, which may be Open or Closed.
•Last Imported: Displays the date on which the information on vulnerabilities was last imported to the system.
•Last Processed: Displays the date the asset was last updated with the most recent information on vulnerabilities associated with it.
•Relevance: Displays the relevance of the asset.