1. Access the Administration module.
2. Select Integration Tasks from the Integrations option on the menu.
3. In the Integration Tasks section, click Create Task.
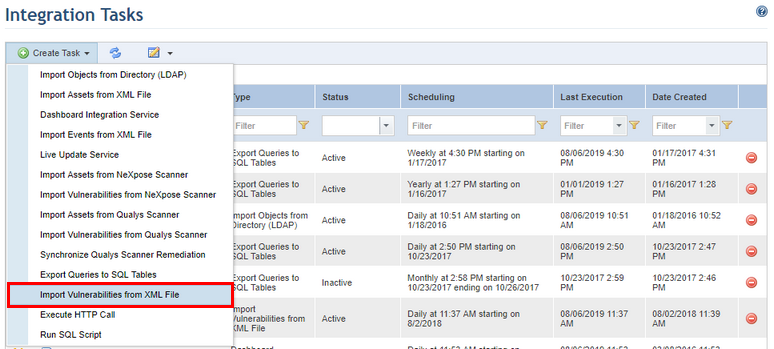
4. Select the Import Vulnerabilities from XML File option from the list that appears (see figure below).

The system displays the form that must be completed to create the new task (see figure below).
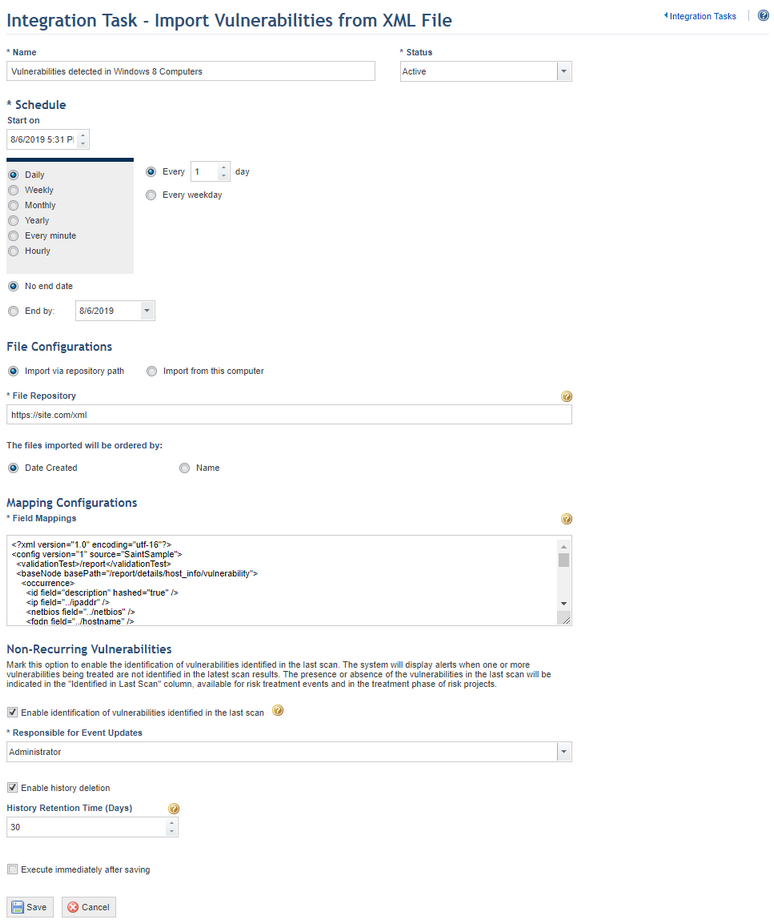
5. In the Name field, enter a name to identify the new integration routine.
6. In the Status field, define the status of the new task. If you select Active, the routine will be activated immediately after it is created. If you select Inactive, the routine will be created but will not function until it is enabled.
7. You can create a schedule for the integration routine in the Schedule section. This step is only applicable if you want to import XML files located in a remote repository. You can skip this step if you want to import XML files directly from your computer, since in this case the task will be executed immediately after being saved. In the Start on field, enter a start date for the integration routine. Next, select one of the options (Daily, Weekly, Monthly, Yearly, Every minute, Hourly), to determine the frequency with which the task will be executed. The task can also be set to run only on weekdays or on weekends as well. In addition, it can be configured to have no end date by clicking the No end date option or configured to end by a certain date by completing the End by field. Note that some integration tasks may take more time to be executed than the option selected, which may result in performance problems.
8. In the File Configurations section, select the Import via repository path option to import XML files that are located in a remote repository, such as a folder on the server or an online file.
9. In the File Repository field, enter the complete path of the repository in which the XML files to be imported are located. This field can be completed with a directory on the server where Modulo Risk Manager is hosted or a remote directory. It is important to ensure that this path is accessible by the service responsible for the integration. In other words, make sure that it is not blocked by firewalls or other devices.
10. Mark the Date Created option so that files are imported according to their creation date, from oldest to most recent. To order the files according to their names when they are imported, mark the Name option. In this case, you can change the names of the files to create a sequence, for example 001_name.xml, 002_name.xml, and so on.
11. Again in the File Configurations section, select the Import from this computer option if you want to import XML files that are stored on the computer where the integration task is being created.
12. In the Select the files to be imported field, click Browse and select the XML files that contain the vulnerabilities you want to import. The size of each file must not exceed 20 MB.
13. After selecting the files, click Import File.
The files are displayed in a list below (see figure below).
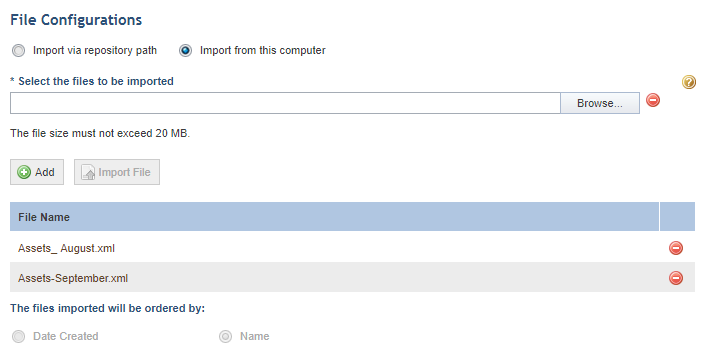
14.
To delete a file, click Delete ( ) next to its name.
) next to its name.
15. The Name option is selected by default for the The files imported will be ordered by field. This ensures that the XML files located on your computer will be imported in alphabetical order.
16. In the Mapping Configurations section, enter the XML code that will allow the integration service to understand the structure of the XML files and map the properties of the vulnerabilities in the file to the properties of the vulnerabilities in the system.
17. In the Alerts on Non-Recurring Vulnerabilities section, mark the Enable system alerts checkbox if you want the system to display notifications when a vulnerability that was imported through the task being created and later sent to treatment is not found in a subsequent execution of this task. These notifications will appear in the risk project through which the vulnerability was sent to treatment, in the Home module for the user that was assigned as project leader, and in the Progress and Associations tabs of the event created to treat the vulnerability.
18. The progress of events will be updated if the vulnerabilities being treated were not identified in the most recent scan results. In the Responsible for Event Updates field, select a system user to be listed in the Updated By field in the Progress tab for this type of event update.
19. Mark the Enable history deletion checkbox if you want the system to automatically delete the execution history of the integration task after a certain number of days.
20. In the History Retention Time (Days) field, enter the number of days after which the history will be deleted. Note that the automatic deletion of the history deletes all of the task execution entries except for the most recent one.
21. Mark the Execute immediately after saving checkbox if you want the system to execute the task once it is saved. For subsequent executions, the system follows the schedule set for the task.
22. When finished, click Save. If you want to quit the operation, click Cancel.
The system displays a success message.