1. Access the Organization module.
2. Select Manage Assets from the Assets option on the menu.
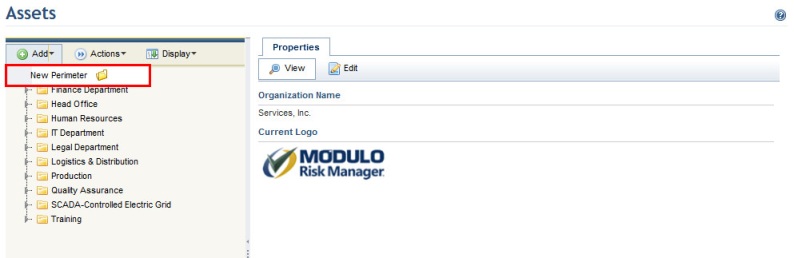
3. In the Assets section, click Add and then select the New Perimeter option (see figure below).

Note: Based on this new perimeter, additional sub-perimeters can be created for it by right-clicking the mouse on the perimeter in which you want to include a sub-perimeter and repeating step 3. The maximum number of sub-perimeters is 100.
The system displays the new perimeter in the organizational structure (see figure below) and automatically fills out some information. By default, the name of the new perimeter will be “New Perimeter”, and the person assigned as responsible for it will be its author.
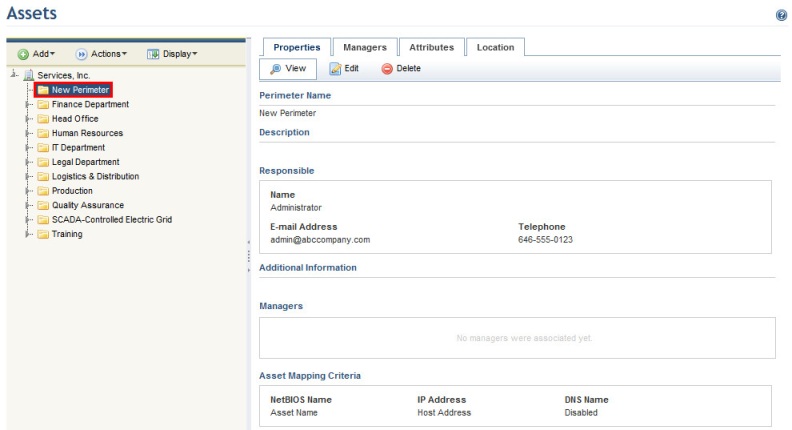
4. To edit the properties, click Edit on the Properties tab.
The system displays a screen where its properties can be edited (see figure below).
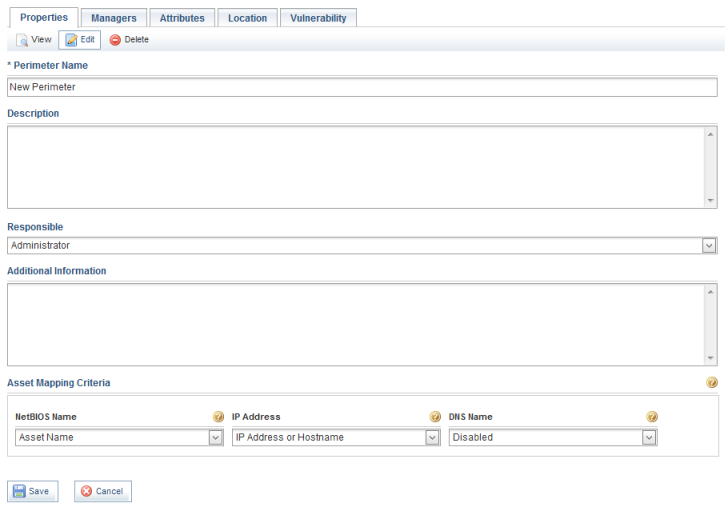
5. In the Perimeter Name field, enter a name for the perimeter.
6. In the Description field, enter information about the perimeter.
7. In the Responsible field, select a person previously registered in the system who will be responsible for the perimeter. This person will be responsible for monitoring activities related to risk and compliance management for the perimeter’s assets and asset components. By default, no system privilege is granted to this this role, and it is used for informational purposes only.
8. In the Additional Information field, enter any other information concerning the perimeter.
9. In the Asset Mapping Criteria section, you can specify which information from which fields in the system will be used to map technology assets from the perimeter and any of its sub-perimeters with machines analyzed by vulnerability scanners. The system can use three pieces of information to correctly match a vulnerability identified by a scanner for a certain machine with the corresponding asset in the system: the NetBIOS name, the IP address, and the DNS name. In some cases, all three must be matched so the vulnerability can be attributed to the correct asset, while in others one is enough to identify it. These fields are optional and should only be used if vulnerabilities will be imported and mapped to assets through integration tasks or manually through the spreadsheet.
10. In the NetBIOS Name field, you can specify which information from which field will be used to map NetBIOS names identified for target machines to assets in the system. The options are:
•Inherited: technology assets this perimeter contains will, by default, inherit their mapping criteria for the NetBIOS name from the parent perimeter. In this case, the default option of mapping NetBIOS names via the assets’ names will apply.
•Disabled: this option disables attempts at mapping through the NetBIOS name, which helps reduce system resource use if you are sure assets can be correctly matched through the IP address or the DNS name alone.
•Asset Name: technology assets this perimeter contains will, by default, be mapped via their names. In this case, the assets’ names in the system must be identical to their NetBIOS names in the scanners.
•Host Address: technology assets this perimeter contains will, by default, be mapped via the information entered in the Host Address field. In this case, the assets’ NetBIOS names in the scanners must be identical to the information entered in the Host Address field from the Properties tab for each asset.
•Technology asset attributes: aside from the above options, this list will also contain the names of any text attributes created for technology assets in the Administration module. In this case, all technology assets this perimeter contains will, by default, be mapped via information entered for the asset attribute selected. The information entered in the attribute fields must then be identical to their NetBIOS names in the scanners.
11. In the IP Address field, you can specify which information from which field will be used to map IP addresses identified for target machines to assets in the system. The options are:
•Inherited: technology assets this perimeter contains will, by default, inherit their mapping criteria from the parent perimeter. In this case, the default option of mapping IP addresses via information entered in the Host Address fields from the Properties tab for each asset apply.
•Disabled: this option disables attempts at mapping through IP addresses, which helps reduce system resource use if you are sure assets can be correctly matched through the NetBIOS or DNS names alone.
•Asset Name: technology assets this perimeter contains will, by default, be mapped via their names. In this case, the assets’ names in the system must be identical to their IP addresses in the scanners.
•Host Address: technology assets this perimeter contains will, by default, be mapped via the information entered in the Host Address field. In this case, the assets’ IP addresses in the vulnerability scanners must be identical to the information entered in the Host Address field from the Properties tab for each asset.
•Technology asset attributes: aside from the above options, this list will also contain the names of any text attributes created for technology assets in the Administration module. In this case, technology assets this perimeter contains will, by default, have their IP addresses mapped via information entered for the asset attribute selected. The information entered in the attribute fields must then be identical to their IP addresses in the scanners.
12. In the DNS Name field, you can specify which information from which field will be used to map DNS names identified for target machines to assets in the system. The options are:
•Inherited: technology assets this perimeter contains will, by default, inherit their mapping criteria from the parent perimeter. In this case, the default option of disabling mapping via DNS names will apply.
•Disabled: this option disables attempts at mapping through DNS names, which helps reduce system resource use if you are sure assets can be correctly matched through the IP addresses or NetBIOS names alone.
•Asset Name: technology assets this perimeter contains will, by default, be mapped via their names. In this case, the assets’ names in the system must be identical to their DNS names in the scanners.
•Host Address: technology assets this perimeter contains will, by default, be mapped via the information entered in the Host Address field. In this case, the assets’ DNS names in the vulnerability scanners must be identical to the information entered in the Host Address field from the Properties tab for each asset.
•Technology asset attributes: aside from the above options, this list will also contain the names of any text attributes created for technology assets in the Administration module. In this case, all technology assets this perimeter contains will, by default, have their DNS names mapped via information entered for the asset attribute selected. The information entered in the attribute fields must then be identical to their DNS names in the scanners.
13. When finished, click Save. If you want to quit the operation, click Cancel to discard the changes.
The system displays a success message and displays the updated properties of the perimeter.