1. Access the Administration module.
2. Select Obsolete Elements from the Settings option on the menu.
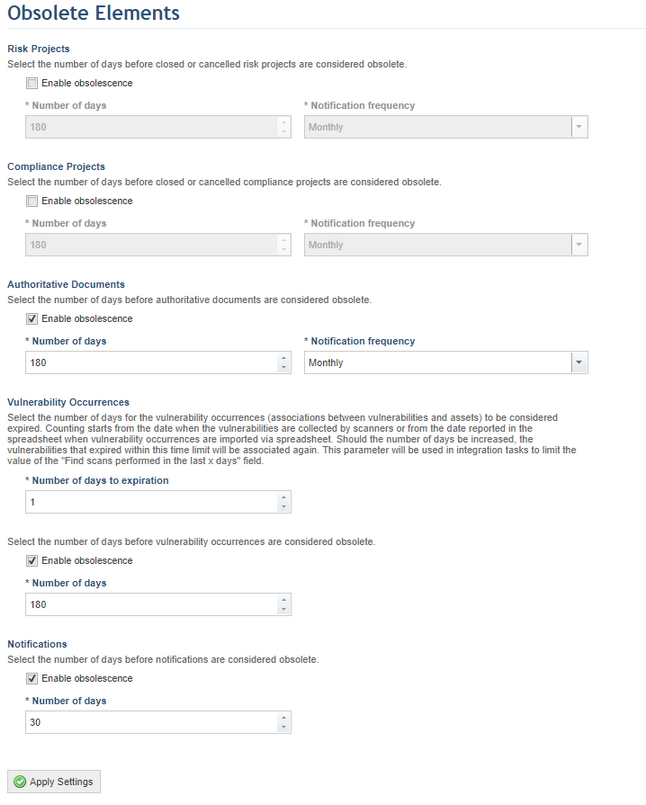
The system displays a screen where you can set a time period for projects and authoritative documents to become obsolete as well as the notification frequency. In addition, you can set time limits for the expiration and deletion of vulnerability occurrences and configure the number of days after which notifications will become obsolete and be deleted (see figure below).

3. In the Risk Projects, Compliance Projects, or Authoritative Documents section, mark the Enable obsolescence checkbox if you want projects or documents to be considered obsolete after a certain number of days, and then enter a time period in the Number of days field, which by default is set to 180 days. Next, in the Notification frequency field select the frequency with which you want notifications to be sent via e-mail, which by default is set to monthly. These notifications will also be displayed in the Notifications section of the Home module.
4. In the Vulnerability Occurrences section, in the Number of days to expiration field, enter the number of days after which the vulnerability occurrences (associations between vulnerabilities and assets) will expire. By default, this time limit is set to 180 days.
Note: After the expiration time, the vulnerabilities will remain in the catalogue, but will no longer be associated with assets in the Organization module and, when processed in existing risk projects, the Risk Score will be calculated normally for them, while in new risk projects the vulnerabilities will not be included in the analysis. If the expiration time is increased, the vulnerability occurrences that had previously expired will again be associated with their related assets, and the countdown for them to expire again (within the new time limit) will begin from the date on which they were registered. The registration date of vulnerability occurrences can be the date when they were collected by scanners or the date entered on the Info worksheet of the spreadhseet template to import vulnerability occurrences. The number of days configured for the expiration of vulnerability occurrences will also be used to define the maximum number of days accepted by the "Find scans performed in the last x days" field displayed in integration tasks that import vulnerabilities into the system.
5. Mark the Enable obsolescence checkbox if you want vulnerability occurrences to become obsolete and to be deleted from the system after a specified number of days. Once enabled, select the number of days in the Number of days field. By default, this number is set to a minimum of 180 days.
Note: Vulnerability occurrences will be deleted permanently, while vulnerabilities will continue to be registered in the catalogue of vulnerabilities of the Knowledge module. If vulnerability occurrences are deleted after their respective vulnerabilities are analyzed in a risk project, the project will continue to display the calculated metrics and the vulnerabilities. However, the vulnerabilities for which the occurrences were deleted will not be included in new risk projects. In addition, their associations with treatment events will always remain.
6. In the Notifications section, mark the Enable obsolescence checkbox if you want the notifications displayed in the Home module to be deleted after a certain time period. Next, in the Number of days field, define the number of days after which the notifications registered in the system will be permanently deleted. By default, this time limit is set to 30 days.
7. When finished, click Apply Settings.
The system displays a success message. If obsolescence was enabled for risk and compliance projects or authoritative documents, a link to obsolete projects and authoritative documents will be displayed in the Risk, Compliance, and Knowledge modules.