This topic explains how to import occurrences of previously registered vulnerabilities identified in assets from the organizational structure. Also explained are the procedures to complete the spreadsheet correctly so that it can be imported successfully.
It is important to note that the spreadsheet template can only import vulnerability occurrences from one source at a time. Occurrences from different sources must be imported separately, using one spreadsheet per source.
The template contains three worksheets, two of which require completion:
•Info: where information on the template itself is provided, including its version and language, as well as where you can specify the source of vulnerabilities and the date and time of completion of the spreadsheet.
•Instructions: where instructions are provided on how to complete each field.
•Associations: where you can indicate which technology assets contain the occurrences being imported.
1. Access the Risk module.
2. Select Import Occurrences from the Vulnerability Occurrences option on the menu.
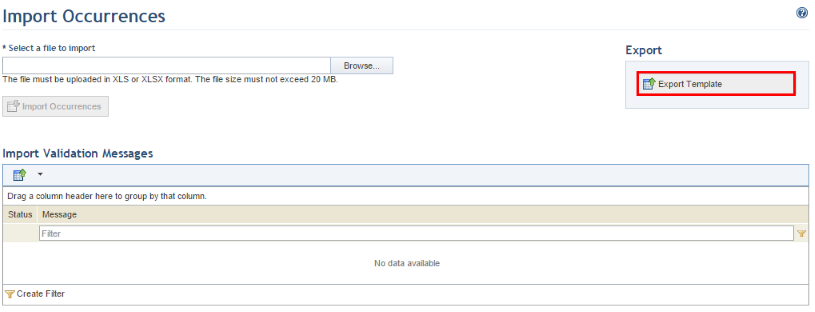
3. In the Import Occurrences section, click the Export Template link in the upper right corner to obtain the formatted Excel spreadsheet that allows vulnerability occurrences to be imported to the system (see figure below).

4. In the dialog box that appears, save the file to your computer and open it.
When the file opens, the template is displayed in Microsoft Excel (see figure below).
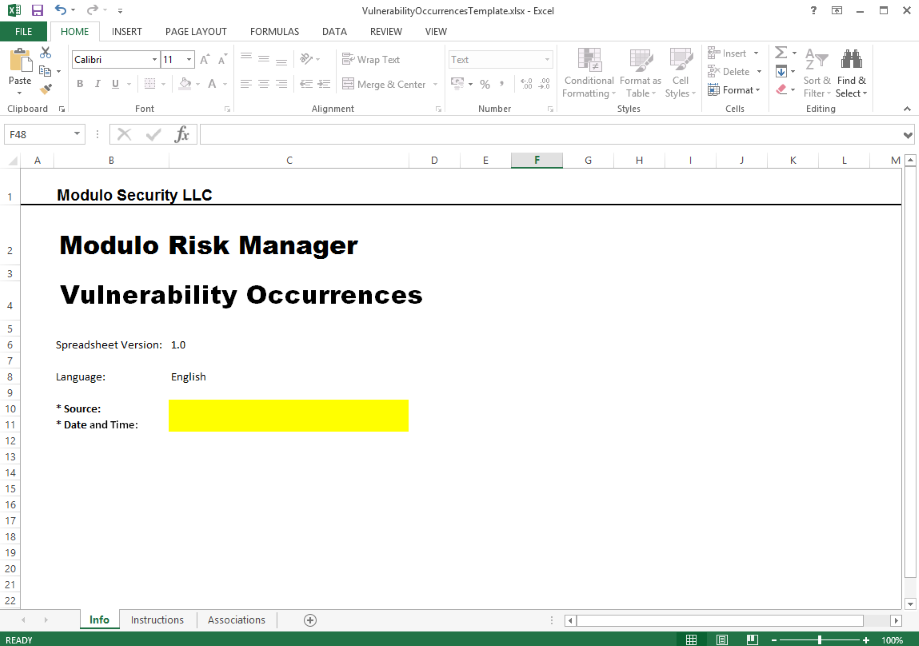
5. In the Info worksheet, specify the source (scanner) of the occurrences being imported in the Source field. This value should match the value listed in the Source column for the corresponding vulnerabilities in the Catalogue of Vulnerabilities section of the Knowledge module. Keep in mind that there is only one Source field for the entire spreadsheet, meaning that you can only import occurrences from one source at a time. Note that values corresponding to scanners integrated with the system ("Qualys Guard" and "NeXpose") will prevent the spreadsheet from being imported, as occurrences identified by these are automatically registered in the system through integration tasks in the Administration module.
6. Next, in the Date and Time field, enter the date and time on which the spreadsheet was completed. The completion format varies according to the regional settings of your computer. For computers set to English (United States), the following format must be used: mm/dd/yyyy hh:mm tt. This field is used to prevent outdated information from being registered, as the system will only import a spreadsheet with a more recent date and time than the last spreadsheet imported. For this reason, be careful when completing this field, as an error could prevent future occurrences from being imported. For example, inserting "01/01/2041 00:00" instead of "01/01/2014 00:00" will cause the system to reject any future spreadsheets dated 2014.
7. Click the Associations worksheet to begin mapping occurrences of vulnerabilities to technology assets in the organizational structure (see figure below).
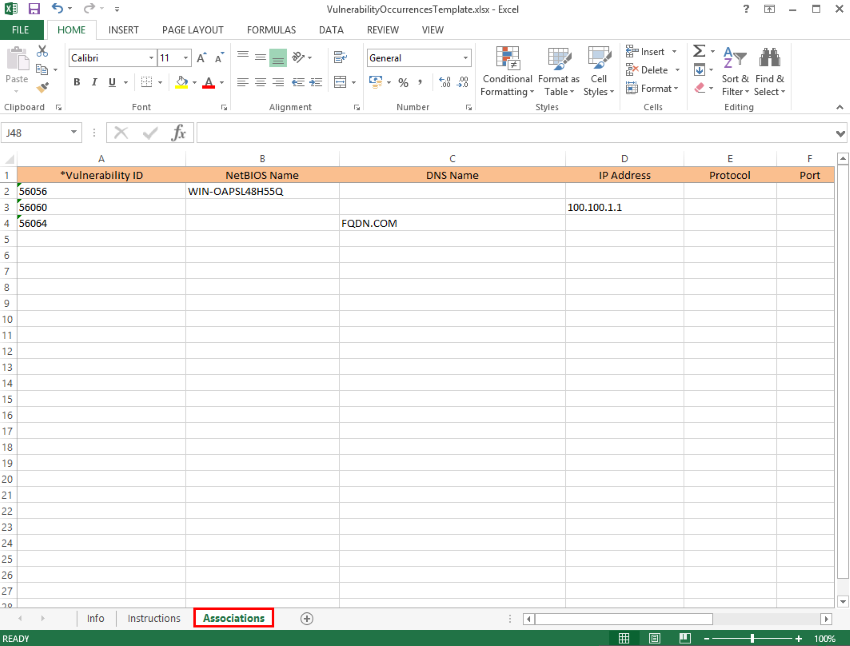
The table below explains how the fields in the Associations worksheet must be completed:
|
Field |
Instructions |
|
*Vulnerability ID |
Enter the ID of the vulnerability occurrence being imported, as listed in the Catalogue of Vulnerabilities section of the Knowledge module, where each vulnerability must have been previously registered. This field is required. |
|
NetBIOS Name |
This field is used to map occurrences of vulnerabilities to technology assets and should be completed with the NetBIOS name of the asset that contains the occurrence being imported. At least one of the "NetBIOS Name", "DNS Name", or "IP Address" fields must be completed for each row, depending on the mapping criteria set for the asset in the Organization module, where it must have been previously registered. |
|
DNS Name |
This field is used to map occurrences of vulnerabilities to technology assets and should be completed with the DNS name (for example, name.domain.com) of the asset that contains the occurrence being imported. At least one of the "NetBIOS Name", "DNS Name", or "IP Address" fields must be completed for each row, depending on the mapping criteria set for the asset in the Organization module, where it must have been previously registered. |
|
IP Address |
This field is used to map occurrences of vulnerabilities to technology assets and should be completed with the IP address of the asset that contains the occurrence being imported. At least one of the "NetBIOS Name", "DNS Name", or "IP Address" fields must be completed for each row, depending on the mapping criteria set for the asset in the Organization module, where it must have been previously registered. |
|
Protocol |
Enter the network protocol associated with the vulnerability occurrence (for example, TCP). |
|
Port |
Enter the TCP or UDP port where the vulnerability occurrence was identified using a number from 0 to 65535. |
|
Evidence |
Provide evidence of the occurrence of the vulnerability in the asset. This field accepts free text. |
8. When finished, save the file to your computer.
9. Access the Risk module.
10. Select Import Occurrences from the Vulnerability Occurrences option on the menu.
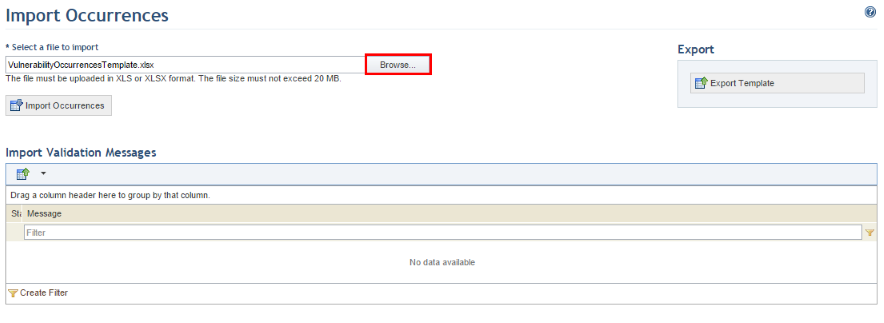
11. In the Import Occurrences section, click Browse (see figure below).
12. Locate the file in the dialog box that appears and click Open.
13. Click Import Occurrences.
Any errors identified will be listed in the Import Validation Messages section, in which case you must return to the spreadsheet and correct each of them. If no errors are found, the system displays a success message.