
•Web-based: The system is fully web-based. Developed based on Microsoft’s .NET architecture, it can be installed locally or securely accessed remotely (with authentication and encryption). Users can access the system through a standard browser.

•Interface: Intuitive and customizable interface includes standardized alerts, messages, workflows, and wizards to guide users. There is also context-sensitive help for specific fields and pages, and the full user manual is available by clicking the Help link in the upper right corner of any page in the system.
•Multilingual Support: The system interface can be displayed in English, Portuguese, or Spanish. There is also support for DBCS (double-byte character sets) for languages such as Japanese and Korean.
•Web Services and Cloud Computing: The system can be provided on a traditional intranet or through an Application Service Provider (ASP), located in an external datacenter or on the cloud.
•Database Encryption: The product supports encryption of stored data. This requires Microsoft SQL Server 2012 (or higher), which offers the TDE (Transparent Data Encryption) feature. If enabled, all information stored by the system in the database will be protected while the information is being recorded and then automatically decrypted when the page is read. SQL Server allows administrators and developers to choose from among several encryption algorithms. For details on the algorithms supported by your SQL Server version, see https://docs.microsoft.com/en-us/sql/relational-databases/security/encryption/choose-an-encryption-algorithm.
•Digital Certificates: In addition to optional database encryption, the system requires a digital certificate generated by a recognized certifying authority to provide a secure communications channel (HTTPS) between the application and the user’s browser. The system also uses digital certificates for authentication and encryption of sensitive information transmitted between system components.
•Multiple Authentication Modes: In addition to native authentication, which uses a database of usernames and passwords kept in the system, it also supports two other authentication modes: federated authentication and LDAP authentication. Note that although there are no prerequisites for using native authentication (as it does not depend on any component external to the application), it presents less scalability and requires greater overhead to manage it.
Support for federated authentication can be configured during the installation of the system. In this model, the application is no longer responsible for user authentication, as users who try to sign in are automatically redirected to a trusted identity provider so that they can enter their credentials. This identity provider, which can be any federation service based on the WS-Federation or SAML 2.0 standards, then authenticates the user by verifying the usernames and passwords in a directory used as an identity store (for example, Active Directory). An encrypted token is issued that transports messages known as "claims", which contain the information needed to authorize access to the system. The token is sent to the application, where it is decrypted so that the information in the claims becomes available and the user's access is authorized.
In the second model, user credentials are verified in an LDAP server by the system portal.
There is also the option to use digital certificates as two-factor authentication. In this case, the user’s browser presents a digital certificate to the system, which will associate the user with a certain account depending on the association criteria set in the system authentication policy. Note that this method is not supported when using federated authentication.
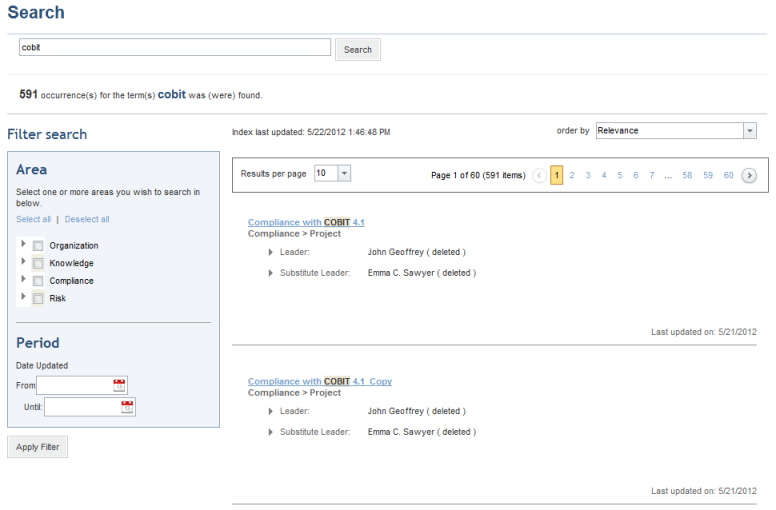
•Indexed Search: This feature allows users to run text queries to locate content stored in the database. Results can be filtered by module (Organization, Knowledge, Compliance, and Risk) and can be configured to only return data that has been updated within a certain period of time. The results obtained can be ordered by relevance or by the date it was last updated, and the number of results per page can also be configured.
•Data Portability: Objects can be exported, edited offline, imported back to the system, or sent in various formats. The system validates information before importing it back to the system and indicates any necessary corrections. Technology assets, groups, and users can also be imported to the system from an external directory.