Unlike permissions granted to profiles, which can be customized freely, only certain permissions can be granted to certain roles. Additional permissions can be granted, but not all. For example, a role can never be granted permission to create an object, since the object must first exist for the role to be assigned to it.
Note that the “Access XYZ Module/Solution” privilege cannot be granted directly to roles. Whenever a user is assigned to a role in a module or solution, this user also needs to be included in a profile that has permission to access the module or solution. For example, if the user "John" was assigned to the role of Perimeter Manager – which is a role from the Organization module –, he must also be included in the Organization Module Users profile or some other profile that has permission to access the Organization module in order to be able to perform the activities related to the assigned role. This is true for all roles from all system modules and solutions.
Also keep in mind that privileges granted to roles take into account an additional context. The same permissions are granted, but only to the objects to which the role was assigned. A profile that receives permission to manage the organizational structure will be able to manage all objects in the organizational structure, whereas this same privilege granted to a role will mean the person or group assigned to the role can only manage objects to which they were assigned.
1. By default, the Perimeter Manager role receives permission to the following privileges:
GENERATE Organizational Reports
MANAGE Organizational Queries
MANAGE the Organizational Structure (see Note 1)
VIEW the Organizational Structure (see Note 1)
2. By default, the Responsible for Asset role receives permission to the following privileges:
MANAGE Organizational Queries
VIEW the Organizational Structure (see Note 2)
3. By default, the Responsible for Business Component role receives permission to the following privileges:
EDIT Business Components
MANAGE Organizational Queries
4. By default, the Responsible for Group of People role receives permission to the following privilege:
MANAGE Groups of People
5. By default, the Organizational Project Leader role receives permissions to the following privileges:
CANCEL Interviews
CLOSE Organizational Projects
DELETE Organizational Projects
EDIT Properties of an Organizational Project
EDIT the Scope of an Organizational Project
SEND Interviews
VIEW Interview Results
VIEW the List and Properties of Organizational Projects
6. By default, the Organizational Project Author role receives permission to the following privileges:
CANCEL Interviews
CANCEL Organizational Projects
CLOSE Organizational Projects
DELETE Organizational Projects
EDIT Properties of an Organizational Project
EDIT the Scope of an Organizational Project
SEND Interviews
VIEW Interview Results
VIEW the List and Properties of Organizational Projects
7. By default, the Organizational Report Template Editor role receives permission to the following privileges:
GENERATE Organizational Reports
MANAGE Organizational Report Templates
8. By default, the Organizational Query Editor role receives permission to the following privilege:
MANAGE Organizational Queries
9. By default, the Asset Risk Analyst role receives permission to the following privileges:
ANALYZE Asset Risks
VIEW List and Properties of Risk Management Projects
VIEW Scope of Risk Management Projects
10. By default, the Leader or Substitute Leader of a Risk Management Project role receives permission to the following privileges:
ANALYZE Asset Risks
CLOSE Asset Risk Analysis
CLOSE Risk Management Projects
EVALUATE Asset Risks
GENERATE Risk Reports
INVENTORY – Edit Analysis Parameters for Risk Management
INVENTORY – Edit Properties of Risk Management Projects
INVENTORY – Edit Scope of Risk Management Projects
MANAGE Risk Queries
MONITOR Treatment Events
REOPEN Asset Risk Analysis
VIEW Analysis Statistics
VIEW List and Properties of Risk Management Projects
VIEW Scope of Risk Management Projects
11. By default, the Risk Project Author role receives permission to the following privileges:
ANALYZE Asset Risks
CANCEL Risk Management Projects
CLOSE Asset Risk Analysis
CLOSE Risk Management Projects
DELETE Risk Management Projects
EVALUATE Asset Risks
GENERATE Risk Reports
INVENTORY – Edit Analysis Parameters for Risk Management Projects
INVENTORY – Edit Properties of Risk Management Projects
INVENTORY – Edit Scope of Risk Management Projects
MANAGE Risk Queries
MONITOR Treatment Events
REOPEN Asset Risk Analysis
VIEW Analysis Statistics
VIEW List and Properties of Risk Management Projects
VIEW Scope of Risk Management Projects
12. By default, the Risk Query Editor role receives permission to the following privileges:
MANAGE Risk Queries
13. By default, the Leader or Substitute Leader of Compliance Project role receives permission to the following privileges:
ANALYZE Compliance
CLOSE Compliance Projects
EVALUATE Non-Compliances
GENERATE Compliance Analysis Reports
INVENTORY – Edit Properties of Compliance Projects
INVENTORY – Edit Requirements of Compliance Projects
INVENTORY – Edit Scope of Compliance Projects
MANAGE Compliance Queries
MONITOR Treatment Events
VIEW List and Properties of Compliance Projects
14. By default, the Compliance Project Author role receives permission to the following privileges:
ANALYZE Compliance
CANCEL Compliance Projects
CLOSE Compliance Projects
DELETE Compliance Projects
EVALUATE Non-Compliances
GENERATE Compliance Analysis Reports
INVENTORY – Edit Properties of Compliance Projects
INVENTORY – Edit Requirements of Compliance Projects
INVENTORY – Edit Scope of Compliance Projects
MANAGE Compliance Queries
MONITOR Treatment Events
VIEW List and Properties of Compliance Projects
15. By default, the Compliance Query Editor role receives permission to the following privilege:
MANAGE Compliance Queries
16. By default, the Responsible for Knowledge Base role receives permission to the following privileges:
EDIT Knowledge Bases
GENERATE Knowledge Base Reports
VIEW History of Knowledge Base Versions
VIEW Knowledge Bases
17. By default, the Responsible for Survey role receives permission to the following privileges:
EDIT Surveys
VIEW Surveys
18. By default, the Responsible for Authoritative Document role receives permission to the following privileges:
EDIT Authoritative Documents
VIEW Authoritative Documents
19. By default, the Event Author role receives permission to the following privileges:
CANCEL Events
CLOSE Events
EDIT Event Coordinator Property
EDIT Event Progress
EDIT Events
EDIT Responsible for Event Property
MANAGE Workflow Queries
VIEW Event History
VIEW Events
20. By default, the Event Coordinator role receives permission to the following privileges:
ASSOCIATE and DISASSOCATE Events
CANCEL Events
CLOSE Events
EDIT Event Coordinator Property
EDIT Event Progress
EDIT Events
EDIT Responsible for Event Property
MANAGE Workflow Queries
VIEW Event History
VIEW Events
21. By default, the Involved in Event role receives permission to the following privileges:
EDIT Event Progress
MANAGE Workflow Queries
VIEW Event History
VIEW Events
22. By default, the Responsible for Event role receives permission to the following privileges:
ASSOCIATE and DISASSOCIATE Events
CANCEL Events
CLOSE Events
EDIT Event Progress
EDIT Events
EDIT Responsible for Event Property
MANAGE Workflow Queries
VIEW Event History
VIEW Events
23. By default, the Event Manager role receives permission to the following privileges:
ASSOCIATE and DISASSOCIATE Events
CANCEL Events
CLOSE Events
DELETE Cancelled Events
EDIT Event Coordinator Property
EDIT Event Progress
EDIT Events
EDIT Responsible for Event Property
EDIT the Event Type
MANAGE Workflow Queries
REOPEN Events
VIEW Event History
VIEW Events
24. By default, the First Reviewer, Second Reviewer, and Third Reviewer roles receive permission to the following privileges:
CANCEL Events
CLOSE Events
EDIT Event Coordinator Property
EDIT Event Progress
EDIT Events
EDIT Responsible for Event Property
MANAGE Workflow Queries
VIEW Event History
VIEW Events
25. By default, the Workflow Query Editor role receives permission to the following privilege:
MANAGE Workflow Queries
26. By default, the Dashboard Author role receives permission to the following privileges:
DELETE Dashboards
EDIT Dashboards
VIEW Dashboards
27. By default, the Audience role (of charts in the Dashboard module) receives permission to the following privilege:
VIEW the List of Charts in the Gallery
28. By default, the Responsible for Policies role receives permission to the following privileges:
EDIT Policies
VIEW Policies
29. By default, the BIA Data Approver role receives permission to the following privilege:
APPROVE Business Component Data
30. By default, the Responsible for Plans role receives permission to the following privileges:
CREATE Events for Plans
EDIT Plans
PUBLISH Plans
VIEW Plans
31. By default, the Substitute Responsible for Plan role receives permission to the following privileges:
CREATE Events for Plans
EDIT Plans
PUBLISH Plans
VIEW Plans
32. By default, the Contingency Staff role receives permission to the following privileges:
CREATE Events for Plans
VIEW Plans
33. By default, the Substitute Contingency Staff role receives permission to the following privileges:
CREATE Events for Plans
VIEW Plans
34. By default, the Responsible for Procedures role receives permission to the following privileges:
EDIT Procedures
PUBLISH Procedures
VIEW Procedures
35. By default, the Risk Owner role receives permission to the following privileges:
EDIT Risks
VIEW Risk Matrix
VIEW Risks
36. By default, the Responsible for Loss Event role receives permission to the following privileges:
DELETE Loss Events
EDIT Loss Events
VIEW Loss Events
37. By default, the Dispatcher role receives permission to the following privilege:
MANAGE Calls
MANAGE Dispatch Requests
38. By default, the Event Report Template Editor role receives permission to the following privileges:
GENERATE Scheduled Event Reports
MANAGE Scheduled Event Report Templates
39. By default, the Responsible for Activity role receives permission to the following privileges:
EDIT Scheduled Events
VIEW Activities
VIEW Scheduled Events
40. By default, the Dashboard Editor role receives permission to the following privilege:
MANAGE Dashboards
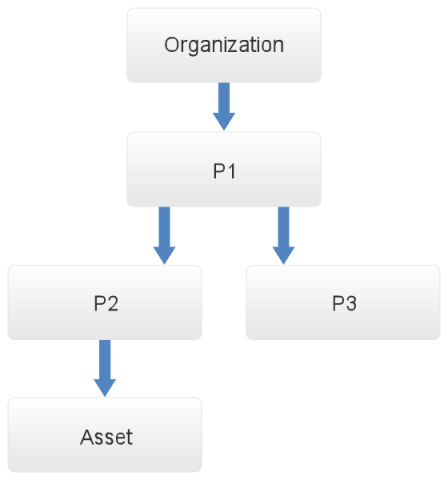
Note 1: By default, the Perimeter Manager role can view and edit the managed perimeters, and view, register, edit, and delete sub-perimeters from within these perimeters, as well as view, register, edit, and delete assets from the managed perimeters. In the example shown in the figure below, the manager of perimeter P2 can view the properties of perimeter P1, and the manager of perimeter P1 can view the properties of P2 and P3.

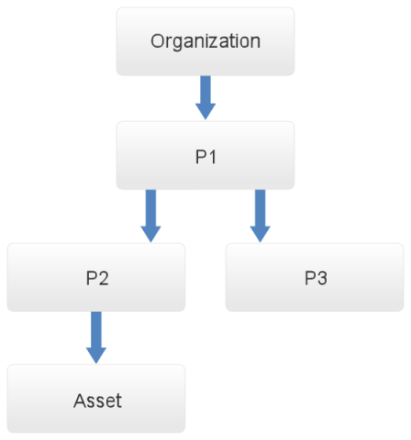
Note 2: By default, the Responsible for Asset role can view the organizational structure. This privilege is applicable only for assets for which the user is responsible. Thus, this role will have a partial view of the organizational structure. In the example shown in the figure below, if the asset is located in perimeter P3, the person responsible for it will be able to view the properties, managers, attributes, location, and vulnerabilities of the parent perimeter P1. Information on the child perimeters where the asset is located cannot be accessed by the person responsible for the asset.